Mondays… amirite? Mondays for IT and Security teams invariably start the same way. The day starts with a dashboard screaming bloody murder, flashing thousands of new alerts. Somewhere in that mess is a potential real threat, but it’s buried under a mountain of noise.
Elevate your application security. Continuously reduce security technical debt.
LUMA.Code Continuous Application Security Testing Platform
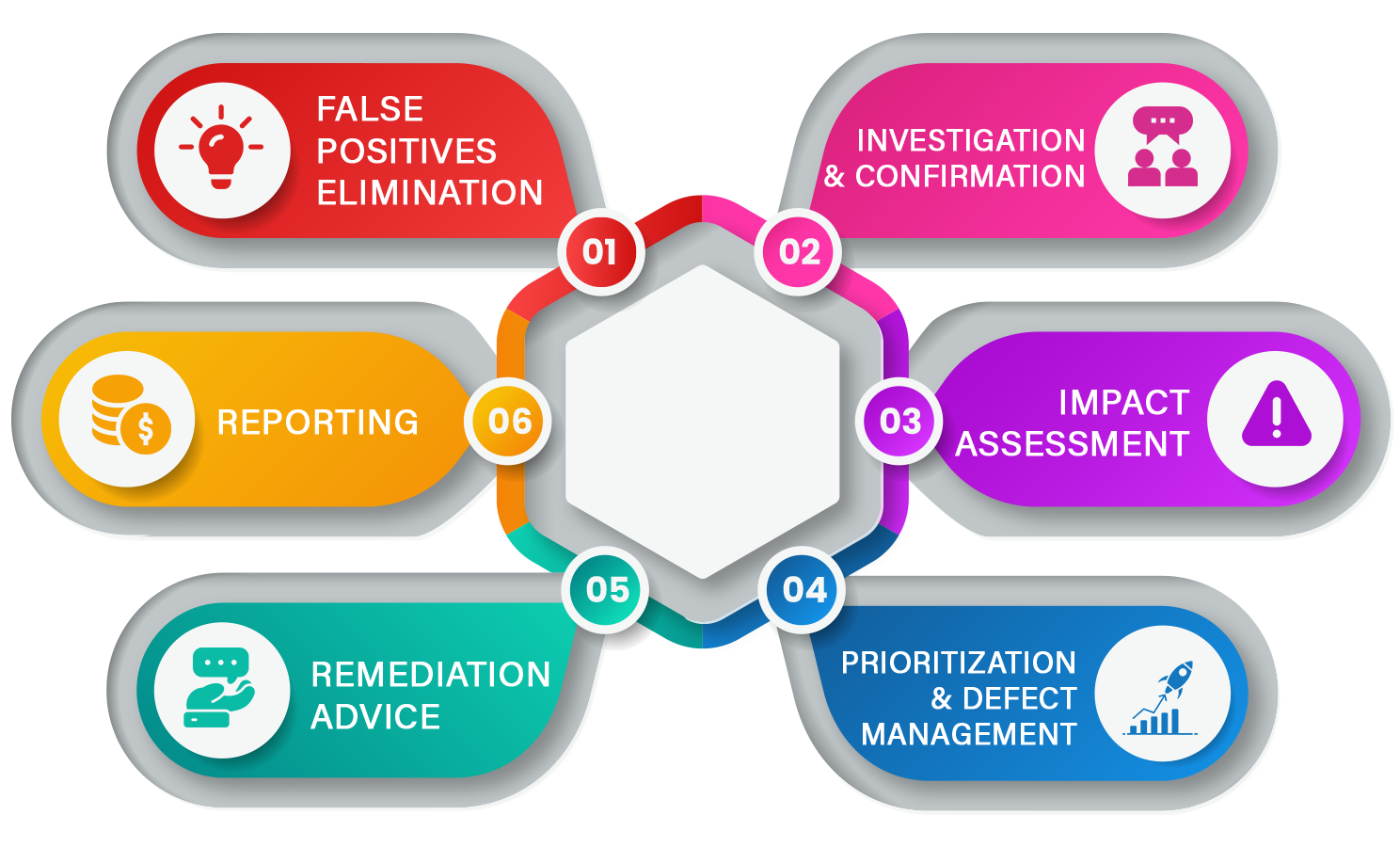
Maintaining the security of your applications is crucial in today’s digital landscape. LUMA.Code continuous application security testing is an expert-augmented platform that provides a comprehensive approach to application security, combining Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), Software Bill of Materials (SBOM), container, and cloud security scanning. We support your development teams with expert triaging, false positive elimination, defect prioritization, and actionable remediation advice.
LUMA.Code allows software development teams to speed up the pace of development while meeting security requirements and reducing security remediation costs. Incorporating all necessary testing technologies, including SAST, SCA, DAST, container and cloud security scanning into a single easy-to-use platform, LUMA.Code delivers managed security testing aligned with NIST SSDF, ISO 27034, and SOC2.
Parabellyx unique approach to defect triaging and actionable remediation advice ensures that the high-priority vulnerabilities are always addressed first in the most efficient manner. LUMA.Code is the most efficient application security testing platform on the market, available to software development organizations offering comprehensive security coverage at a fraction of the cost of an application security FTE.
LUMA.Code Features
Comprehensive Application Security Testing
LUMA.Code platform covers a wide range of security testing methodologies, including SAST for source code analysis, DAST for runtime analysis, SCA for third-party component analysis, SBOM for tracking dependencies and compliance reporting, and container and cloud security scanning to ensure your applications’ security in diverse environments. This comprehensive approach provides a deep understanding of your application’s security posture and potential vulnerabilities.
Expert Triaging & False Positive Elimination
Building on LUMA.Code decision engine, our team of experienced application security professionals conducts expert triaging to ensure that identified vulnerabilities are genuine and require attention. We eliminate false positives, reducing the workload for your development teams and ensuring they can focus on addressing critical security issues.
Defect Prioritization & Actionable Remediation Advice
LUMA.Code expert-augmented platform goes beyond identifying vulnerabilities. We help your development teams prioritize defects based on factors such as potential impact, likelihood, and the effectiveness of existing security controls. We also provide actionable remediation advice to help your teams address vulnerabilities effectively and efficiently, improving your overall application security.
Seamless Integration with Development Processes
LUMA Security platform is designed to seamlessly integrate with your existing development processes, ensuring minimal disruption while enhancing security. By incorporating continuous security testing into your development lifecycle, you can proactively identify and address vulnerabilities, reduce risks, and ensure compliance with industry standards and regulations.
Interested In LUMA.Code Platform?
We’ll help you identify, manage and remediate your code security defects without reducing your application delivery speed.
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.
Recent Blogs
The cybersecurity game is changing at breakneck speed, and businesses are in a constant arms race to protect their digital assets from increasingly sophisticated threats. One of the most effective weapons in this battle? Penetration testing. But not all pen tests are created equal. Some rely purely...
Other LUMA Security Platform Modules

LUMA.Perimeter
Continuous external exposure management and penetration testing module combining attack surface management, exploitability validation, and public data risks analysis.

LUMA.Compliance
ISO 27001, SOC2, CMMC & PCI DSS attestation preparation and continuous compliance management platform. Be prepared for stress-free audits and third-party assessments.
Request our guidance on top cybersecurity priorities
We’ll help you evaluate your cybersecurity strengths and vulnerabilities and guide you through security debt reduction
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.




