Mondays… amirite? Mondays for IT and Security teams invariably start the same way. The day starts with a dashboard screaming bloody murder, flashing thousands of new alerts. Somewhere in that mess is a potential real threat, but it’s buried under a mountain of noise.
Develop a robust cybersecurity strategy
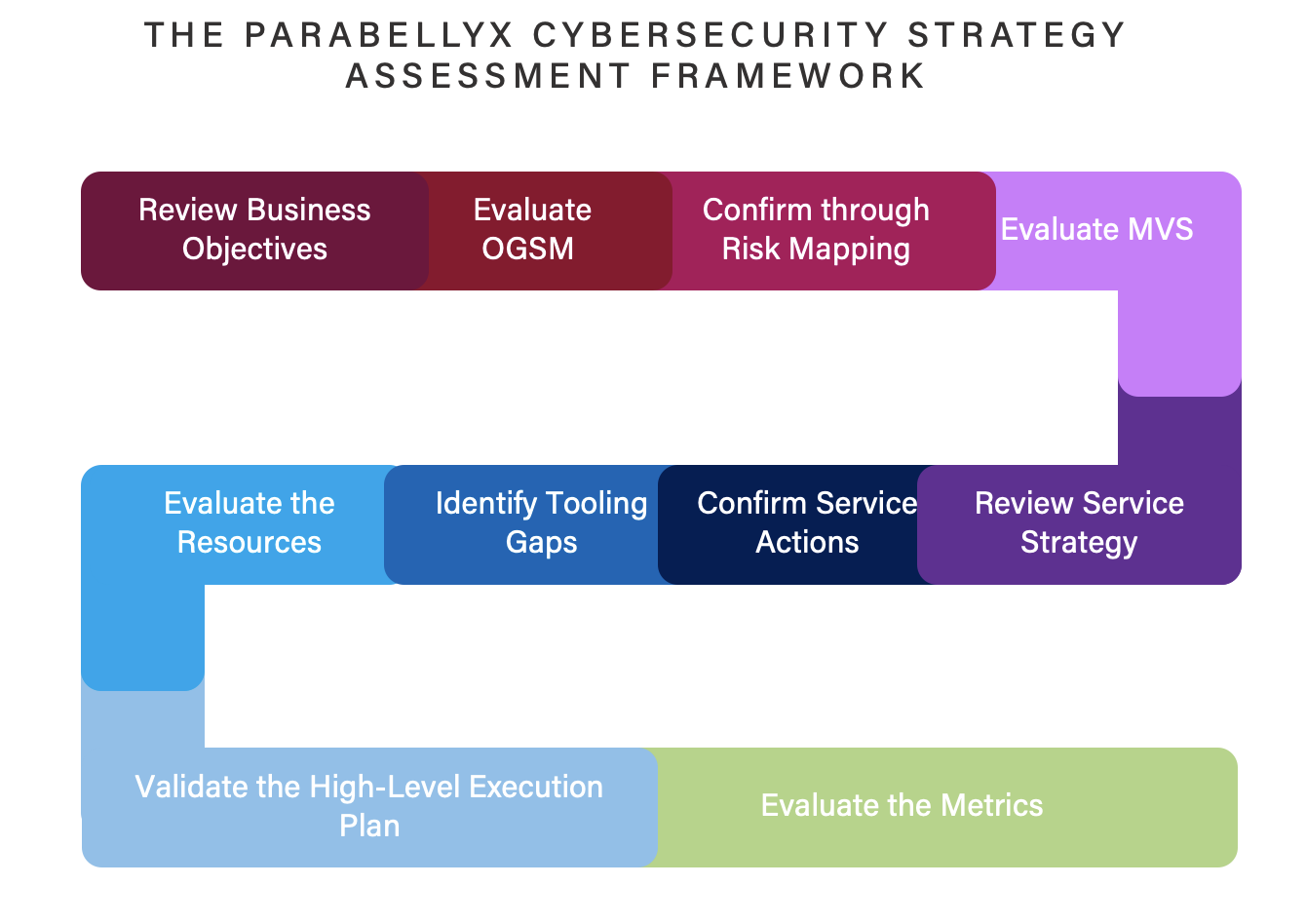
Cybersecurity Strategy Assessment
A successful cybersecurity strategy is essential for protecting your organization’s critical assets and maintaining a competitive edge in today’s digital landscape. Our cybersecurity strategy assessment services combine a risk-based, service delivery approach with lean enterprise principles, providing a comprehensive framework for identifying and prioritizing risks, optimizing resource allocation, and streamlining processes to achieve maximum security and efficiency.
Parabellyx has created a Cybersecurity Strategy Assessment Framework designed to validate the strategic plan and evaluate its effectiveness, combining risk-based and services delivery approach with a lean enterprise methodology to create a plan aligned with business objectives and methodology for elaboration to justify decisions on security capabilities, rationalize technology solutions, and estimate resources and skills required for execution.
Our Strategy Assessment Approach
Alignment with Organizational Objectives and Goals
Cybersecurity Strategy cannot be defined without understanding and alignment with organizational strategic goals. Parabellyx security leadership experts will work to evaluate cybersecurity requirements framed by this grand strategy and address these in a measurable way in the cybersecurity strategy to establish strong link between security and business functions.
Risk-Based & Service Delivery Approach
Our expert team conducts a thorough assessment of your organization’s security posture, identifying and prioritizing risks based on factors such as potential impact, likelihood, and the effectiveness of existing controls. By incorporating a service delivery approach, we ensure that your cybersecurity strategy aligns with your organization’s unique needs, objectives, and risk tolerance.
Lean Enterprise Principles Integration
Incorporating lean enterprise principles into your cybersecurity strategy helps your organization maximize efficiency and minimize waste. Our services assesses alignment with these principles, such as defining a minimum viable service, eliminating redundancies, streamlining processes, and focusing on continuous improvement, to achieve a more agile and resilient security posture.
Resource Optimization & Process Streamlining
Effective resource allocation is critical for maintaining a robust cybersecurity strategy. Parabellyx strategy assessment will help you optimize the use of resources, such as personnel, technology, and budget, ensuring that your organization’s security efforts are focused on the most critical risks and areas of potential impact. By streamlining processes and removing inefficiencies, we help you improve your organization’s overall security posture and efficiency.
Continuous Improvement & Adaptability
A successful cybersecurity strategy must be agile and adaptable in the face of evolving threats and emerging technologies. Parabellyx cybersecurity strategy assessment evaluates your organization in adopting a continuous improvement mindset, regularly reviewing and updating your strategy to ensure ongoing resilience and preparedness for new challenges.
Interested In Our Cybersecurity Strategy Assessment Services?
We’ll help you build a strong and robust cybersecurity program
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.
Recent Blogs
The cybersecurity game is changing at breakneck speed, and businesses are in a constant arms race to protect their digital assets from increasingly sophisticated threats. One of the most effective weapons in this battle? Penetration testing. But not all pen tests are created equal. Some rely purely...
More Governance, Risk & Compliance Solutions
ISO 27001 & SOC 2 Preparation Services
Achieve and maintain compliance with our comprehensive preparation services for ISO 27001 and SOC 2 certifications.

Breach Impact Assessment
Parabellyx created a unique framework to assess an organization's resilience to cyber breaches.
Threat Impact Assessment
Evaluate the potential impact of cyber threats on your organization with our comprehensive threat impact assessment services.
Privacy Impact Assessment
Helpings customers mandated by regulations or following best practices for their services to understand and document the Privacy Impact.
Request our guidance on top cybersecurity testing priorities
We’ll help you evaluate your cybersecurity strengths and vulnerabilities
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.




