Mondays… amirite? Mondays for IT and Security teams invariably start the same way. The day starts with a dashboard screaming bloody murder, flashing thousands of new alerts. Somewhere in that mess is a potential real threat, but it’s buried under a mountain of noise.
Test your entire public attack surface. Every time, all the time.
LUMA.Perimeter Continuous External Exposure Management and Penetration Testing Platform
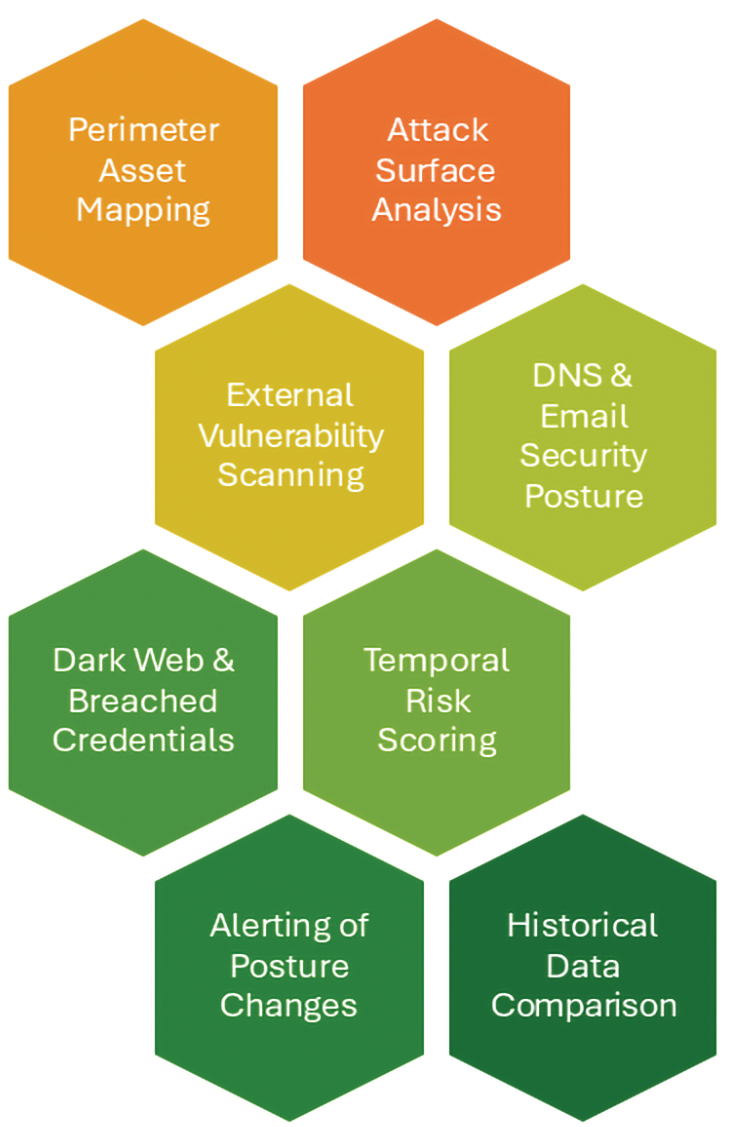
LUMA.Perimeter allows you to detect any security issues with externally exposed services and assets much faster than adversaries would.
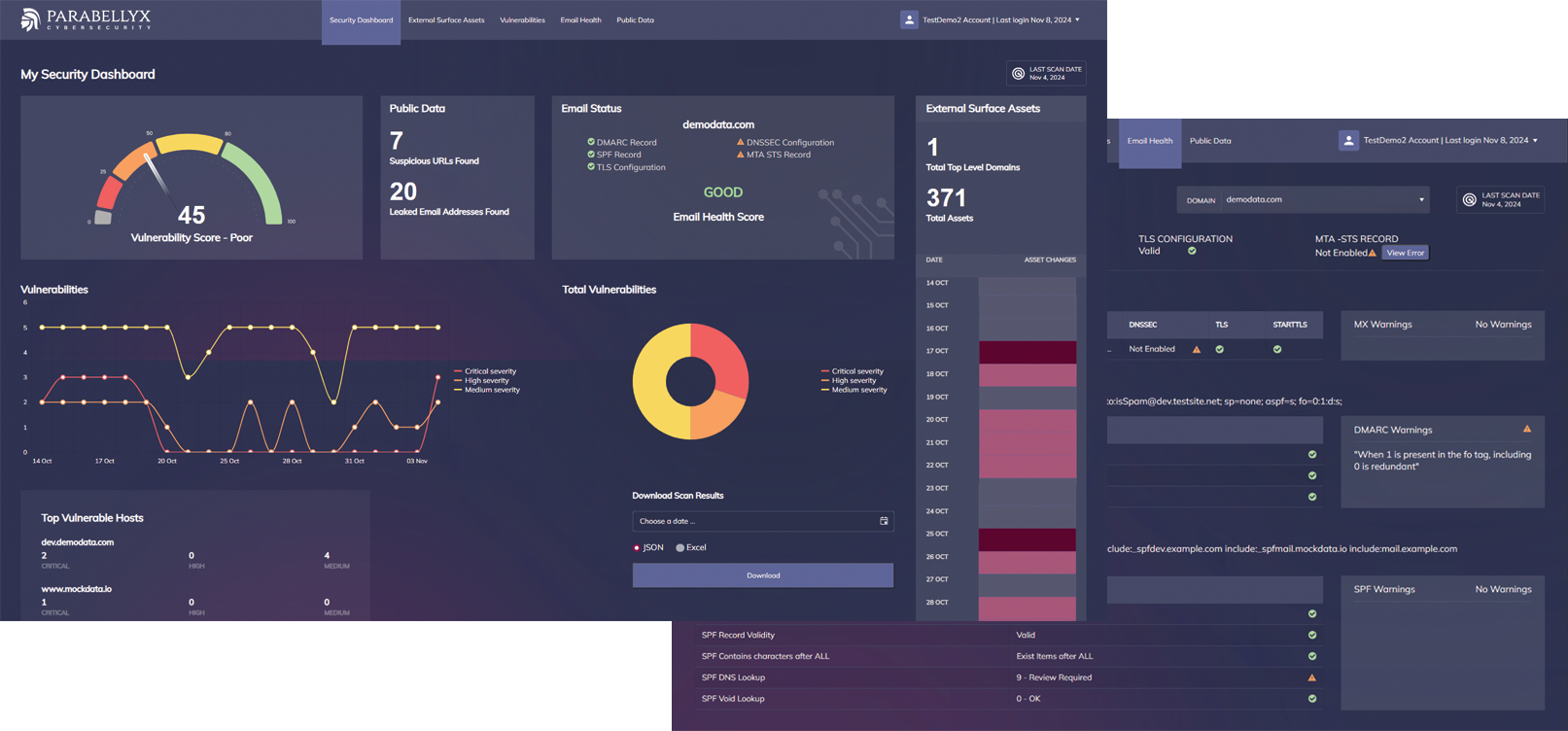
LUMA Security platform combines attack surface management and public risk monitoring with active testing and exploitability analysis. You can monitor any changes to the external digital footprint, test all externally exposed services, keep track of public risks from multiple sources, and maintain a regularly updated penetration testing report.
LUMA.Perimeter platform allows you to track risks, maintain regulatory compliance and continuously test the security of your publicly exposed systems from a single console.
The Benefits of LUMA.Perimeter
Make the security testing a continuous process
Continuously test your externally exposed services against existing and new exploits and attacks.
Detect changes in your attack surface
Maintain a complete perimeter asset mapping and detect changes in your externally exposed assets and services as they occur.
Track public data risks
Be aware of breached credentials, typosquatting and clickjacking risks, DNS and email health and security posture
Make changes with confidence
Ensure that no unwanted services or assets are exposed during the change process. Conduct external penetration testing on the new or changed assets and services immediately.
Maintain trust and compliance
Have a current penetration testing report for your auditors, vendor risk management, and regulators.
Why LUMA.Perimeter?
Track changes to your externally exposed assets, digital footprint and public risks. Conduct daily comprehensive testing and maintain an up-to-date penetration testing report. Get support and guidance on resolving detected security issues.
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.
Use Cases
Monitor the attack surface
Be constantly aware of all changes to your publicly exposed services, both on-premise and in the cloud. Prevent breaches through unsanctioned and insecure external services.
Keep track of public risks
Track targeted malicious activity, including breached credentials, domain impersonations and other signs of imminent attacks.
Secure change management
Ensure your planned and emergency changes do not expose additional services and data that are not meant for public access.
Continuously test your external security
Get continuous penetration testing in the context of the new perimeter, which includes identities, the cloud, and all exposed services.
.
Interested In Our LUMA.Perimeter Platform?
We’ll help you detect, test and fix your external security issues before adversaries become aware.
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.
Recent Blogs
The cybersecurity game is changing at breakneck speed, and businesses are in a constant arms race to protect their digital assets from increasingly sophisticated threats. One of the most effective weapons in this battle? Penetration testing. But not all pen tests are created equal. Some rely purely...
Other LUMA Security Platform Modules

LUMA.Code
Continuous application security testing and security debt reduction platform that combines SAST, SCA, SBOM, cloud and container security testing with exploitability-based prioritization and expert-tailored remediation advice.

LUMA.Compliance
ISO 27001, SOC2, CMMC & PCI DSS attestation preparation and continuous compliance management platform. Be prepared for stress-free audits and third-party assessments.
Request our guidance on top cybersecurity testing priorities
We’ll help you evaluate your cybersecurity strengths and vulnerabilities
Heading 1
with a request body that specifies how to map the columns of your import file to the associated CRM properties in HubSpot.... In the request JSON, define the import file details, including mapping the spreadsheet's columns to HubSpot data. Your request JSON should include the following fields:... entry for each column.




